
MULKASE:一种针对多个所有者数据的新型密钥聚合可搜索加密方法(英文).docx

快乐****蜜蜂



在线预览结束,喜欢就下载吧,查找使用更方便
相关资料

MULKASE:一种针对多个所有者数据的新型密钥聚合可搜索加密方法(英文).docx
MULKASE:一种针对多个所有者数据的新型密钥聚合可搜索加密方法(英文)Title:MULKASE:ANewKeyAggregationsearchableencryptionmethodforMulti-ownerDataAbstract:Astherapidgrowthofdataiswitnessedinvariousfields,theneedforefficientandsecuredatasharingamongmultipleownershasbecomeincreasinglyimpor

面向无线传感器网络的密钥聚合授权可搜索加密方法.pdf
本发明公开面向无线传感器网络的密钥聚合授权可搜索加密方法,基于密钥聚合可搜索加密KASE技术和属性基加密ABE技术,通过只分发单个聚合可搜索密钥实现数据所有者与授权查询用户共享加密数据,而查询用户只需要向云服务器提交一个陷门来执行关键字搜索。只有当授权的聚合可搜索密钥满足数据所有者定义的访问策略时才能对共享的加密数据执行关键字搜索。本发明给出了通用架构和形式化安全证明,以及实例化构造。实验分析表明,与现有方案对比,本发明方案具有较高的计算效率,解决了现有大多数密钥聚合可搜索加密方案容易遭受“密钥伪造攻击”
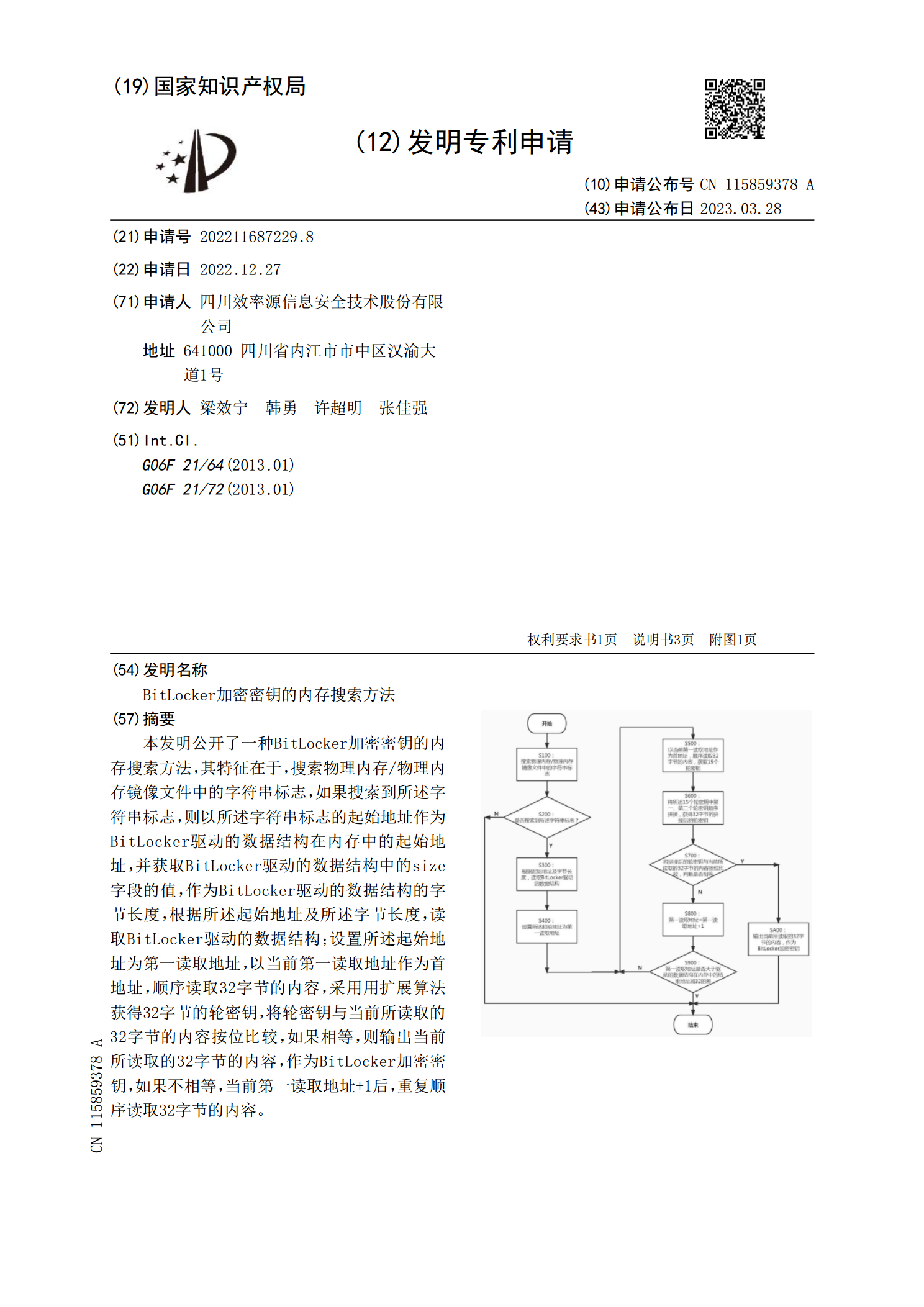
BitLocker加密密钥的内存搜索方法.pdf
本发明公开了一种BitLocker加密密钥的内存搜索方法,其特征在于,搜索物理内存/物理内存镜像文件中的字符串标志,如果搜索到所述字符串标志,则以所述字符串标志的起始地址作为BitLocker驱动的数据结构在内存中的起始地址,并获取BitLocker驱动的数据结构中的size字段的值,作为BitLocker驱动的数据结构的字节长度,根据所述起始地址及所述字节长度,读取BitLocker驱动的数据结构;设置所述起始地址为第一读取地址,以当前第一读取地址作为首地址,顺序读取32字节的内容,采用用扩展算法获得3

基于区块链的分类医疗数据可搜索加密方法.pdf
本发明公开了一种基于区块链的分类医疗数据可搜索加密方法,包括:步骤1、系统初始化;步骤2、密钥生成与用户注册;步骤3、密文生成以及存储;步骤4、陷门生成;步骤5、密文搜索与共享。该方法能够满足第三方数据用户对不同敏感等级的医疗数据的搜索需要,同时提高可搜索加密方案的安全性,并降低计算与存储开销。

量子对称加密密钥的搜索方法、装置、设备及介质.pdf
本申请涉及一种量子对称加密密钥的搜索方法、装置、设备及介质。该方法基于H门和旋转门将初始量子态转化为初始密钥叠加态,使用基态编码对明文进行编码得到明文量子态,使用预设的对称加密算法构建的量子加密电路加密明文量子态得到密文量子态,根据测量密文量子态的结果和明文的真实密文构建损失函数,调节初始旋转门的旋转角度参数使损失函数满足预设条件,确定此时旋转门的旋转角度参数,结合H门将初始量子态转换为搜索密钥叠加态,确定测量搜索密钥叠加态的结果中出现次数最多的密钥为搜索得到的密钥,实现通过量子计算的方式加密和测量,并使
